Google hacking, also named Google dorking, is a hacker technique that uses Google Search and other Google applications to find security holes in the configuration and computer code that websites use.
“Google hacking” involves using advanced operators in the Google search engine to locate specific strings of text within search results. Some of the more popular examples are finding specific versions of vulnerable Web applications. A search query with intitle:admbook intitle:Fversion filetype:php would locate all web pages that have that particular text contained within them. It is normal for default installations of applications to include their running version in every page they serve, for example, “Powered by XOOPS 2.2.3 Final”.
Which Dorks Are the Most Powerful?
By far, the most severe kind of exposed file we can find is one that leaks the credentials to user accounts or the entire service itself. Usually, this will happen in one of two ways. In the first, a server or other service is set up incorrectly and exposes its administrative logs to the internet. When passwords are changed, or a user fails to log in correctly, these logs can leak the credentials being used to the internet.
The other way this happens is when configuration files that contain the same information are exposed. These are files that are supposed to be internal but are often leave critical information out in the open. Either one of these mistakes can cause the entire service to be taken over by an attacker who happens to chance upon the information.
We’ll be using Google dorks to find not only these files, but also things like file transfer servers that may contain interesting information, email lists, and my personal favorite, exposed webcams.
To follow along, you’ll need a browser with internet access. The beautiful thing about using Google dorks is that we can use tools accessible by nearly anyone to find vulnerable systems.
Once you have a browser open, navigate to Google.com, and we can get started.
Step 1 Finding FTP Servers & Websites Using HTTP
To start, we’ll use the following dork to search for file transfer servers published sometime this year. Searching for these servers can allow us to find files that are supposed to be internal, but were unknowingly made public.
intitle:"index of" inurl:ftp after:2018
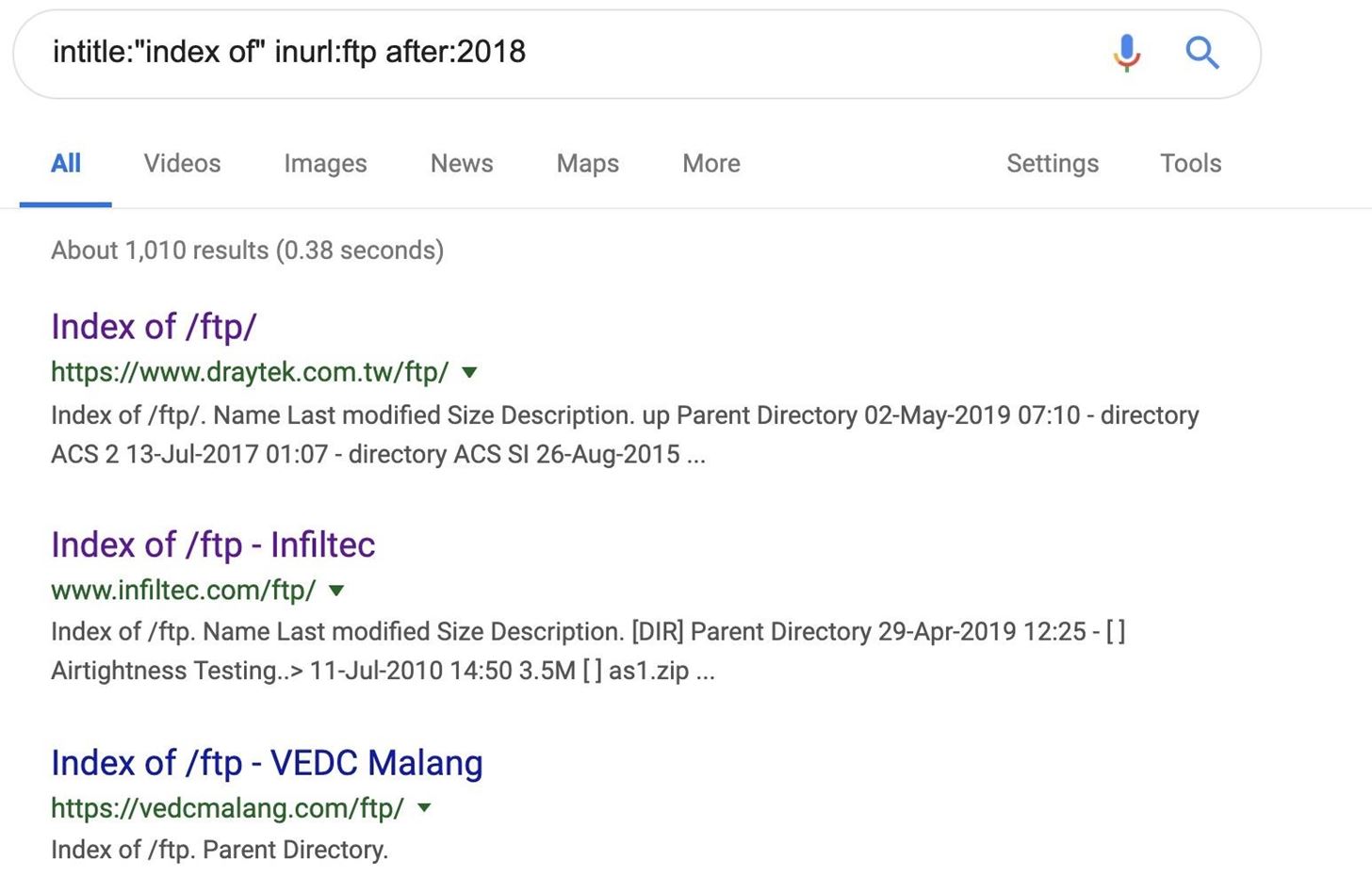
These servers become public because the index file of their FTP server is the kind of data that Google loves to scan — a fact people tend to forget. Google’s scanning leads to a complete list of all the files contained within the server being searchable on Google.
If we want to find insecure webpages still using HTTP to poke at, we can modify the command slightly to do so by changing the “ftp” to “http” and re-running the search.
intitle:"index of" inurl:http after:2018
Searching that string should produce a list of lots and lots of websites using HTTP, ready to be attacked. But if we’re looking for a specific type of site, we can go even further.
If we want to start attacking some easy targets, we can be more specific and search for online forms still using HTTP by changing the text in the search title.
intitle:"forum" inurl:http after:2018
We can keep adding search operators like AND inurl:”registration” to get more specific and hunt down the registration pages of insecure form websites.
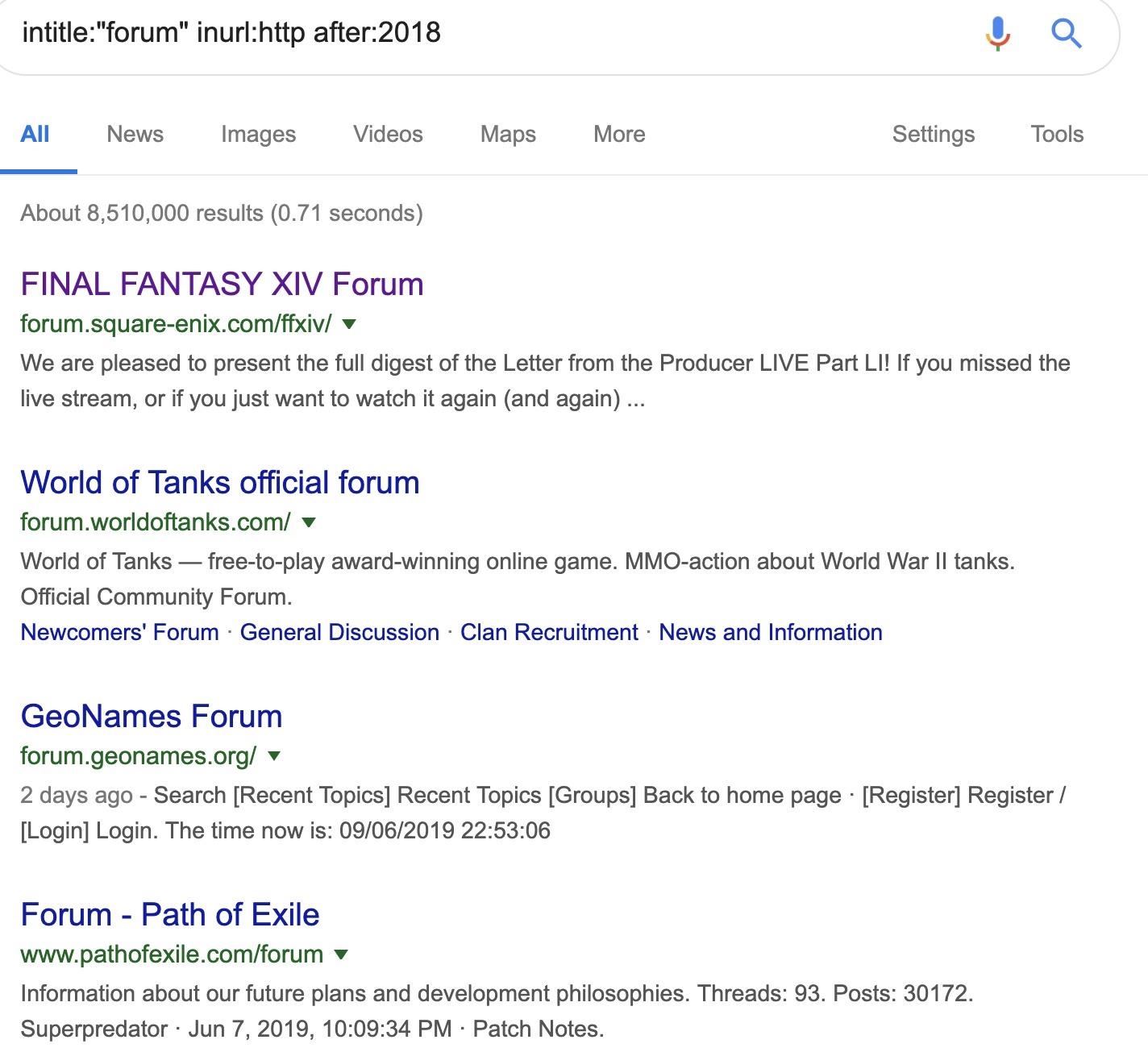
Here you can see we’ve found a list of vulnerable online forums using HTTP.
Step 1:Find Log Files with Passwords
The next step will be to search for files of the .LOG type. Searching for LOG files will allow us to look for clues about what the credentials to the system or various user or admin accounts might be.
The dork we’ll be using to do this is as follows.
allintext:password filetype:log after:2018
When searching for current log files exposed to the internet, we find this almost immediately.
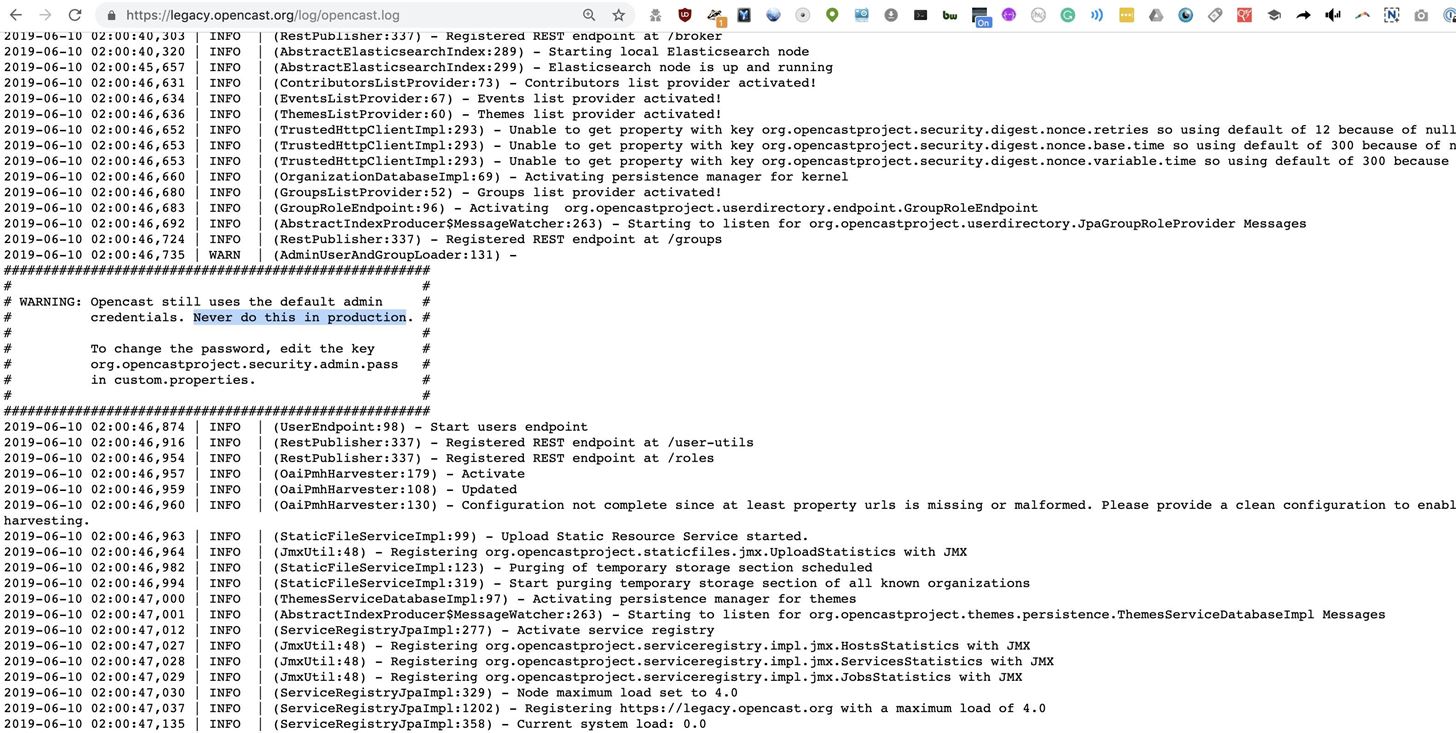
This log states that the password is the default one, which takes just a simple Google search of the OpenCast Project website to discover. With one search, we’ve possibly found the credentials to this system without hacking anything at all.
Step 2 Find Configuration Files with Passwords
Configuration files should not be public pretty much ever, and .ENV files are great examples of this. If we search for .ENV files that contain a string for the database password, we instantly find the password to this database we’ve discovered.
filetype:env "DB_PASSWORD" after:2018
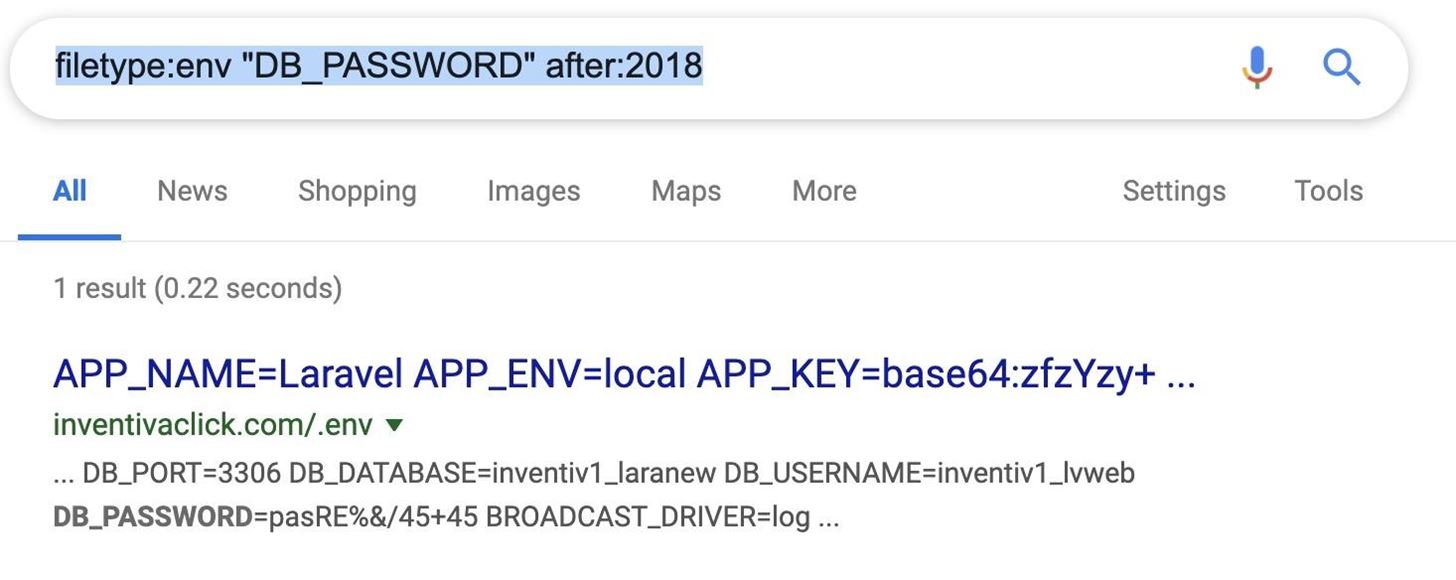
If we remove the after:2018 we can see older log files also exposing services to the internet.
Step 3 Find Email Lists
Email lists are a great way of scraping email addresses and trying to find information on corporate or school targets. These lists are frequently exposed by companies or schools that are trying to organize email lists for their members.
To find them, we’ll be looking for spreadsheet .XLS file type with the string “email.xls” in the URL.
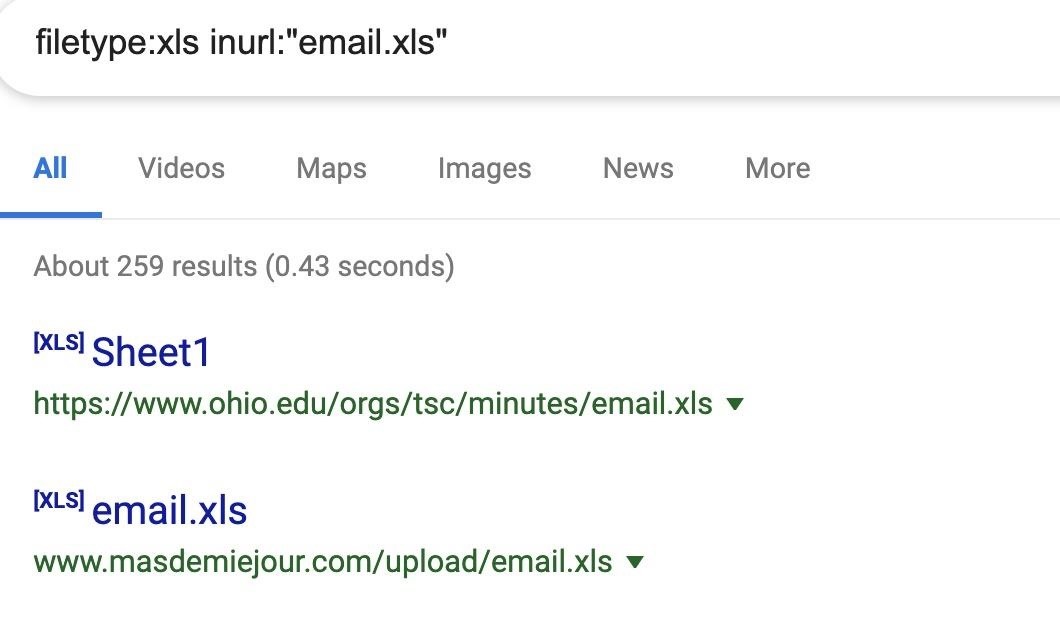
While these results are useful, be careful not to download any file without first considering if it’s a honeypot. Many people will take popular dorks and then leave a server hosting a file that looks vulnerable but could instead contain malware.
Finally, if you thought Shodan was the only service that can find weird open cameras, you were dead wrong. Camera login and viewing pages are usually HTTP, meaning Google is happy to index them and provide them for viewing if you know the right search string.
One common format for webcam strings is searching for “top.htm” in the URL with the current time and date included. You’ll find a lot of results this way.
inurl:top.htm inurl:currenttime
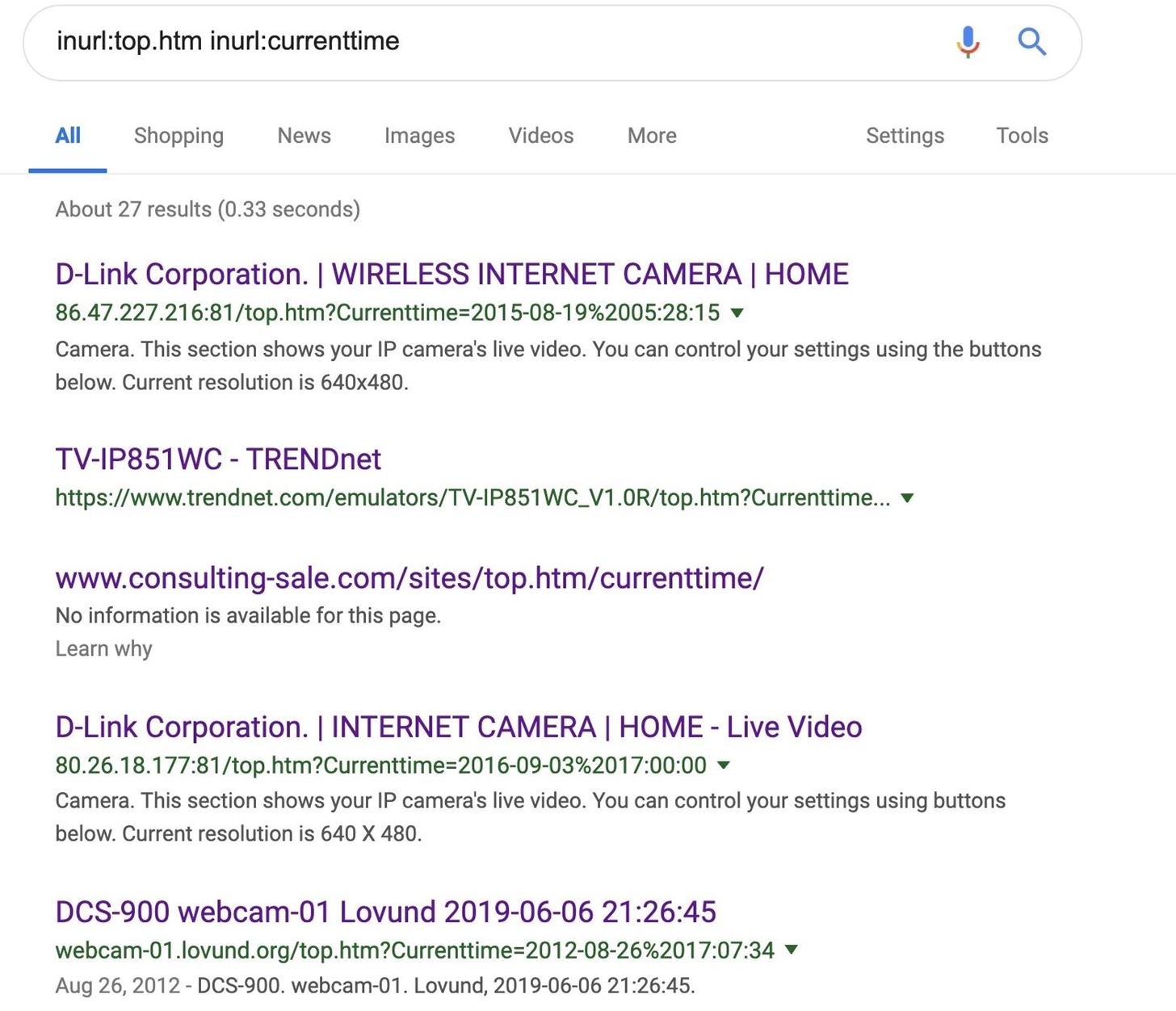
The first result is a webcam that appears to be the Windows XP background from another angle in Belmullet, Ireland.

Another dork for cameras that produces outstanding results searches for a common live-view page hosted on routers.
inurl:"lvappl.htm"
Using this dork, I was able to locate the best camera of all, the birdcam1.
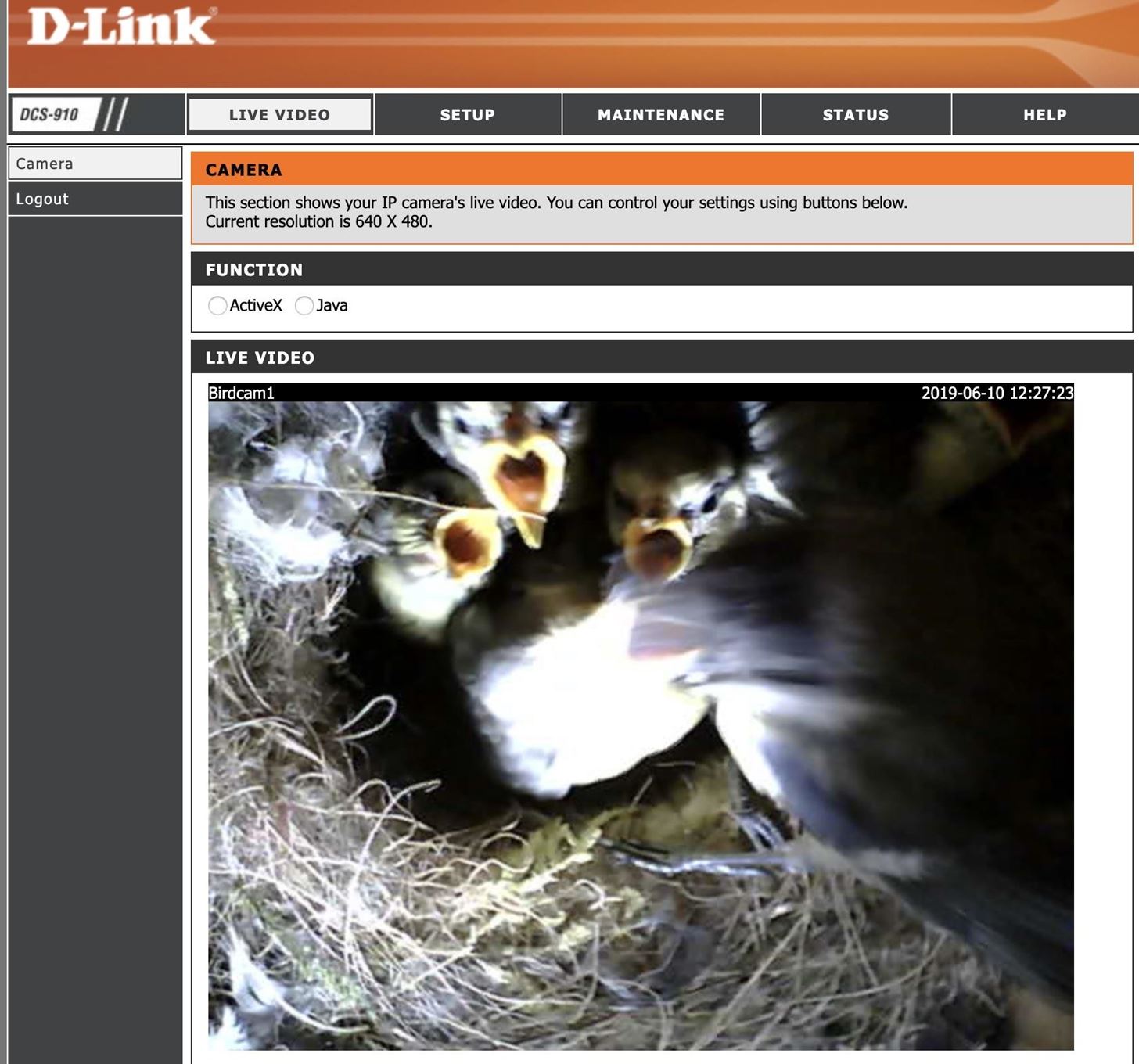
Please do not hack the bird cam, but feel free to enjoy it here. Many other cameras are available, though all are less interesting than birdcam1.

Many cameras also monitor inside factories or industrial areas.
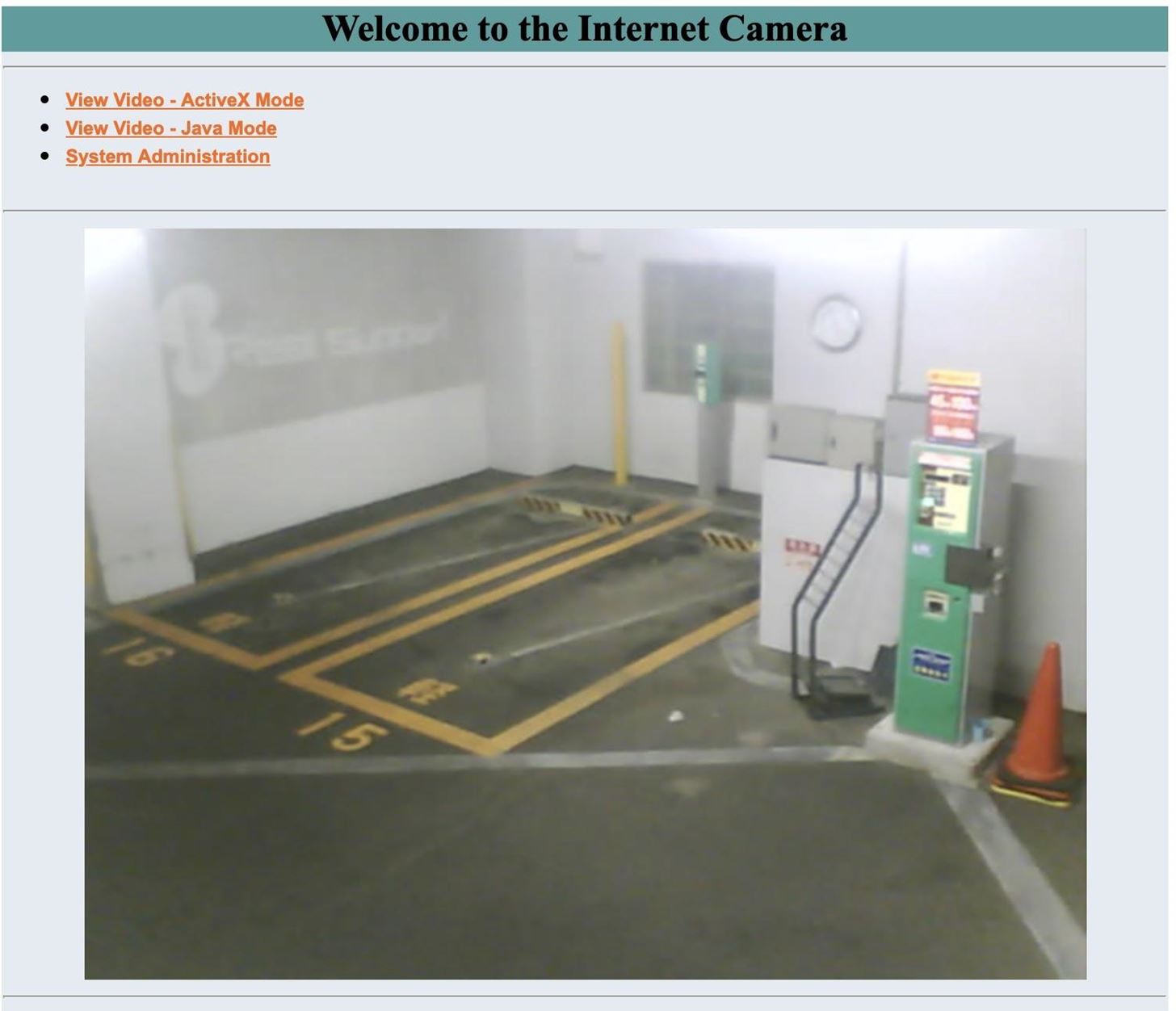
While you can view the cameras I demonstrated without a password; many dorks look for webcam login pages that have a well-known default password. This tactic, while illegal, allows easy access to many webcams not intended for public viewing.
reference: null byte and exploit-db
for more :https://www.exploit-db.com/


Leave a comment